SpringBoot整合springsecurity+oauth2.0 本文采用的springboot去整合springsecurity,采用oauth2.0授权认证,使用Jwt对token增强。本文仅为学习记录,如有不足多谢提出。 OAu
本文采用的springboot去整合springsecurity,采用oauth2.0授权认证,使用Jwt对token增强。本文仅为学习记录,如有不足多谢提出。
OAuth 2.0是用于授权的行业标准协议。OAuth 2.0为简化客户端开发提供了特定的授权流,包括WEB应用、桌面应用、移动端应用等。
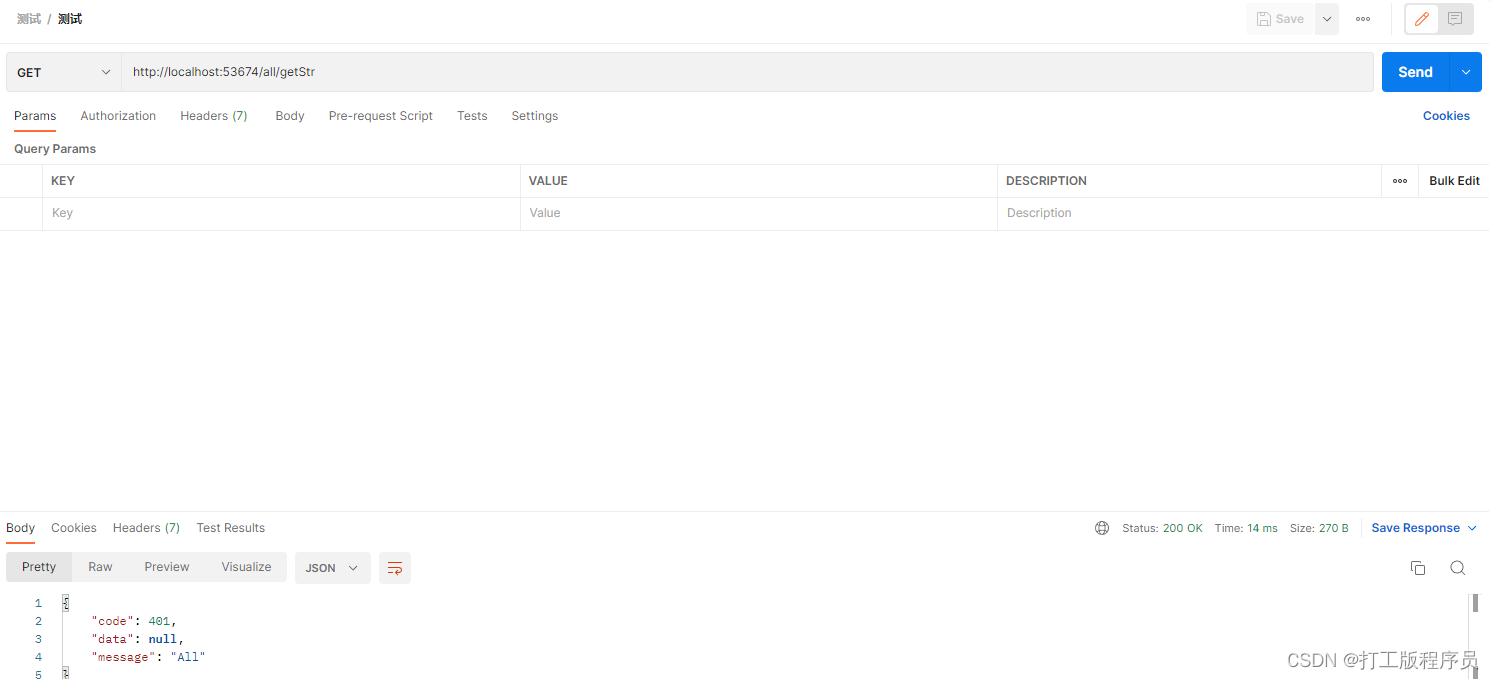
org.springframework.boot spring-boot-starter-security org.springframework.security.oauth spring-security-oauth2 2.2.6.RELEASE org.springframework.security spring-security-jwt 1.1.0.RELEASE #本文采用的springboot版本为2.6.3,由于Spring Security 在 Spring Boot 2.7.0 中已弃用的 WebSecurityConfigurerAdapter 所有在配置。所以在配置SpringSecurity配置时,原先configure采用bena配置SecurityFilterChain beanpackage com.example.health.model;import com.alibaba.fastJSON.annotation.jsONField;import lombok.Data;import org.springframework.security.core.GrantedAuthority;import org.springframework.security.core.authority.SimpleGrantedAuthority;import org.springframework.security.core.userdetails.UserDetails;import java.util.Collection;import java.util.Set;@Datapublic class SecurityUser implements UserDetails { private Long userId; private String username; private Long deptId; private String password; private Boolean enabled; private Collection authorities; private Set permissions; public SecurityUser() { } @Override public Collection getAuthorities() { return this.authorities; } @Override public String getPassword() { return this.password; } @Override public String getUsername() { return this.username; } @JSONField(serialize = false) @Override public boolean isAccountNonExpired() { return true; } @Override public boolean isAccountNonLocked() { return true; } @Override public boolean isCredentialsNonExpired() { return true; } @Override public boolean isEnabled() { return this.enabled; }} package com.example.health.model.dto;import lombok.Builder;import lombok.Data;import lombok.EqualsAndHashCode;@Data@EqualsAndHashCode(callSuper = false)@Builderpublic class Oauth2TokenDto { private String token; private String refreshToken; private String tokenHead; private int expiresIn;}package com.example.health.security.handle;import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;import com.example.health.common.constant.MessageConstant;import com.example.health.mapper.SysUserMapper;import com.example.health.model.SecurityUser;import com.example.health.model.entity.SysUser;import org.springframework.beans.BeanUtils;import org.springframework.beans.factory.annotation.Autowired;import org.springframework.security.core.userdetails.UserDetails;import org.springframework.security.core.userdetails.UserDetailsService;import org.springframework.security.core.userdetails.UsernameNotFoundException;import org.springframework.stereotype.Service;import java.util.Objects;@Servicepublic class UserServiceImpl implements UserDetailsService { @Autowired private SysUserMapper sysUserMapper; @Override public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException { SysUser sysUser = sysUserMapper.selectOne(new QueryWrapper().lambda().eq(SysUser::getUserName, username)); if (Objects.isNull(sysUser)) { throw new UsernameNotFoundException(MessageConstant.USERNAME_PASSWORD_ERROR); } SecurityUser securityUser = new SecurityUser(); BeanUtils.copyProperties(sysUser, securityUser); securityUser.setEnabled(!Objects.equals(0, sysUser.getStatus())); return securityUser; }} @Componentpublic class AuthenticationEntryPointImpl implements AuthenticationEntryPoint, Serializable { private static final long serialVersionUID = -8970718410437077606L; @Override public void commence(httpservletRequest request, HttpServletResponse response, AuthenticationException authException) throws IOException, ServletException { int code = HttpStatus.UNAUTHORIZED; String msg = String.fORMat("请求访问:%s,认证失败,无法访问系统资源", request.getRequestURI()); ServletUtils.renderString(response, JSON.toJSONString(ResultUtils.error(code, msg))); }}@Componentpublic class JwtTokenEnhancer implements TokenEnhancer { @Override public OAuth2AccessToken enhance(OAuth2AccessToken accessToken, OAuth2Authentication authentication) { SecurityUser securityUser = (SecurityUser) authentication.getPrincipal(); Map info = new HashMap<>(); //把用户ID设置到JWT中 info.put("user_id", securityUser.getUserId()); ((DefaultOAuth2AccessToken) accessToken).setAdditionalInformation(info); return accessToken; }} @AllArgsConstructor@Configuration@EnableAuthorizationServerpublic class Oauth2Config extends AuthorizationServerConfigurerAdapter { private PasswordEncoder passwordEncoder; private UserServiceImpl userDetailsService; private AuthenticationManager authenticationManager; private JwtTokenEnhancer jwtTokenEnhancer; @Override public void configure(ClientDetailsServiceConfigurer clients) throws Exception { clients.inMemory() .withClient("client-app") .secret(passwordEncoder.encode("123456")) .scopes("all") .authorizedGrantTypes("password", "refresh_token") .accessTokenValiditySeconds(3600) .refreshTokenValiditySeconds(86400); } @Override public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception { TokenEnhancerChain enhancerChain = new TokenEnhancerChain(); List delegates = new ArrayList<>(); delegates.add(jwtTokenEnhancer); delegates.add(accessTokenConverter()); enhancerChain.setTokenEnhancers(delegates); //配置JWT的内容增强器 endpoints.authenticationManager(authenticationManager) .userDetailsService(userDetailsService) //配置加载用户信息的服务 .accessTokenConverter(accessTokenConverter()) .tokenEnhancer(enhancerChain); } @Override public void configure(AuthorizationServerSecurityConfigurer security) throws Exception { security.allowFormAuthenticationForClients(); } @Bean public JwtAccessTokenConverter accessTokenConverter() { JwtAccessTokenConverter jwtAccessTokenConverter = new JwtAccessTokenConverter(); jwtAccessTokenConverter.seTKEyPair(keyPair()); return jwtAccessTokenConverter; } @Bean public KeyPair keyPair() { //从classpath下的证书中获取秘钥对 KeyStoreKeyFactory keyStoreKeyFactory = new KeyStoreKeyFactory(new ClassPathResource("jwt.jks"), "123456".toCharArray()); return keyStoreKeyFactory.getKeyPair("jwt", "123456".toCharArray()); }} @Configuration@EnableWebSecuritypublic class SecurityConfig extends WebSecurityConfigurerAdapter { @Autowired private AuthenticationEntryPointImpl unauthorizedHandler; @Bean @Override public AuthenticationManager authenticationManagerBean() throws Exception { return super.authenticationManagerBean(); } @Override protected void configure(HttpSecurity httpSecurity) throws Exception { httpSecurity // CSRF禁用,因为不使用session .csrf().disable() // 禁用HTTP响应标头 .headers().cacheControl().disable().and() // 认证失败处理类 .exceptionHandling().authenticationEntryPoint(unauthorizedHandler).and() // 基于token,所以不需要session .sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS).and() // 过滤请求 .authorizeRequests() // 对于登录login 注册reGISter 验证码captchaImage 允许匿名访问 .antMatchers("/login", "/register", "/captchaImage").permitAll() .antMatchers("/all*.html", "*.CSS", "*.js", "/profileapi-docs", "/druid@RestController@RequestMapping("/oauth")public class AuthController { @Autowired private TokenEndpoint tokenEndpoint; @RequestMapping(value = "/token", method = RequestMethod.POST) public BaseResponse postAccessToken(Principal principal, @RequestParam Map parameters) throws HttpRequestMethodNotSupportedException, HttpRequestMethodNotSupportedException { OAuth2AccessToken oAuth2AccessToken = tokenEndpoint.postAccessToken(principal, parameters).getBody(); Oauth2TokenDto oauth2TokenDto = Oauth2TokenDto.builder() .token(oAuth2AccessToken.getValue()) .refreshToken(oAuth2AccessToken.getRefreshToken().getValue()) .expiresIn(oAuth2AccessToken.getExpiresIn()) .tokenHead("Bearer ").build(); return ResultUtils.success(oauth2TokenDto); }} @RestController@RequestMapping("/all")public class AllController { @GetMapping(value = "/getStr") public BaseResponse getStr() { return ResultUtils.success(“All”); }}@RestController@RequestMapping("/test")public class TestController { @GetMapping(value = "/getStr") public BaseResponse getStr() { return ResultUtils.success("test"); }}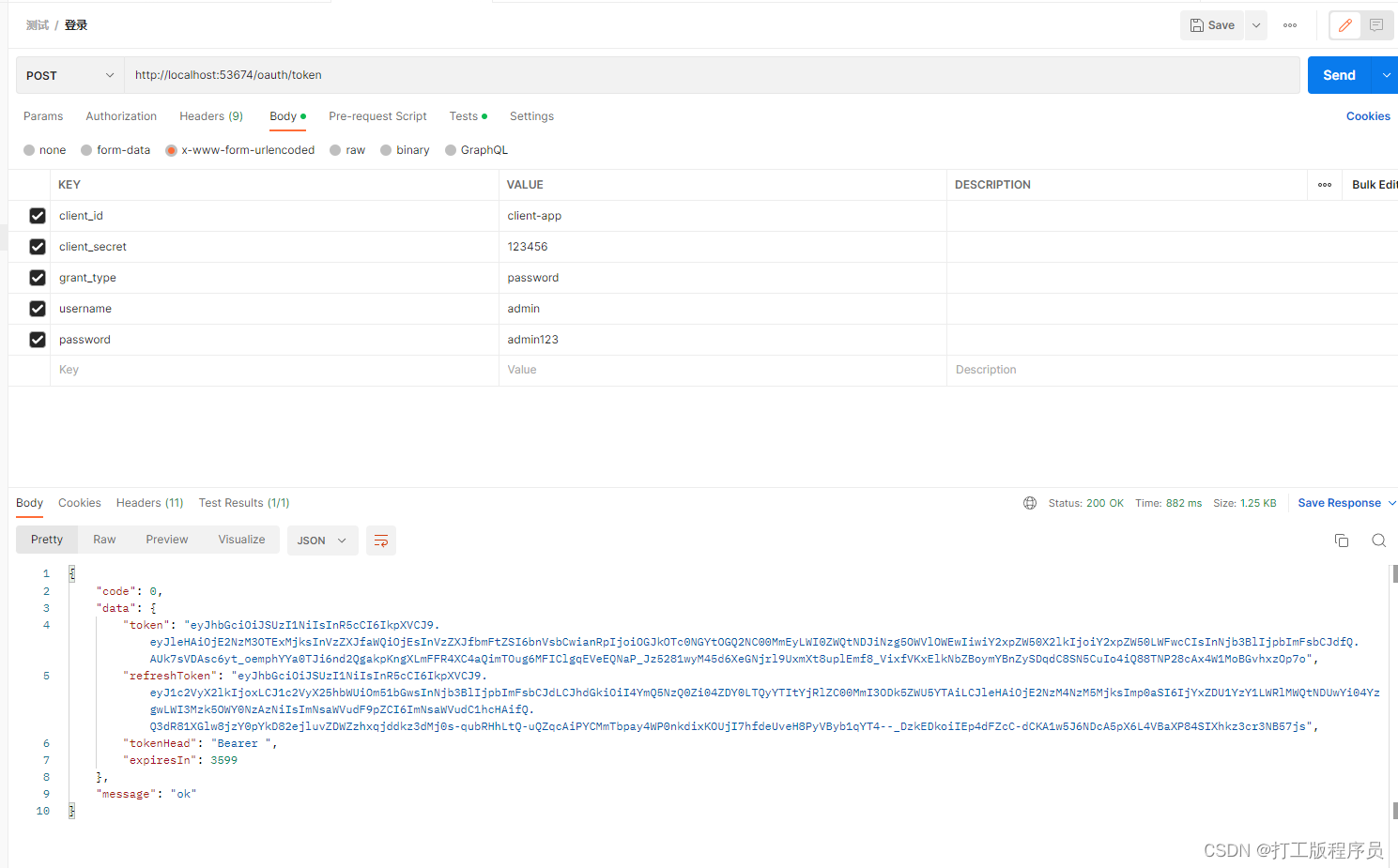

来源地址:https://blog.csdn.net/qq_45072555/article/details/128698253
--结束END--
本文标题: springboot整合springsecurity+oauth2.0密码授权模式
本文链接: https://www.lsjlt.com/news/374361.html(转载时请注明来源链接)
有问题或投稿请发送至: 邮箱/279061341@qq.com QQ/279061341
下载Word文档到电脑,方便收藏和打印~
2024-05-13
2024-05-13
2024-05-11
2024-05-11
2024-05-10
2024-05-07
2024-04-30
2024-04-30
2024-04-30
2024-04-29
回答
回答
回答
回答
回答
回答
回答
回答
回答
回答
0